Cross-chain bridges support asset interoperability between different blockchains. These bridges are the talk of the town for providing an efficient method to transfer cross-chain assets. However, a complex workflow involving both on-chain smart contracts and off-chain programs gives birth to several security issues. Numerous cyber-attacks targeted cross-chain bridges, in which hackers stole billions of dollars.
Security Issues in Cross-Chain Bridges
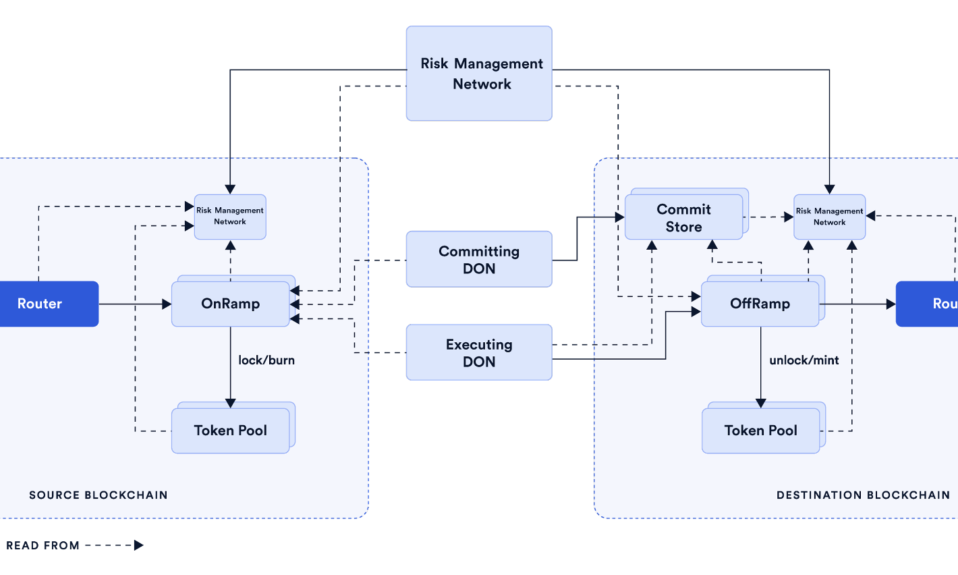
Cross-chain bridges work as intermediaries allowing users to lock their assets; tokens on different blockchains. Moreover, these bridges are responsible for validating these locked tokens. Users can perform cross-chain trading, deposit, or swap through these bridges.
However, various types of cross-chain bridge bugs affect the normal functionality and security of the entire system, allowing hackers to steal data or assets. A few of their associated vulnerabilities are as follows.
- Occasionally, the vulnerabilities can be in the smart contract code, which hackers can easily exploit to gain access to the network and perform fraudulent transactions.
- There can be inconsistency between on-chain and off-chain components, which can impact the normal functioning of the bridge, and attackers can take advantage of it.
- If there is any bug in the validation logic of the bridge, hackers can perform false transactions, stealing users’ assets.
- If the infrastructure of the bridges contains any vulnerability, hackers can quickly get access to the network to steal assets.
Secure Cross-Chain Bridges from Bugs and Hackers
Cross-chain bridge hacks can be reduced if developers take serious care while developing the code. The next step to ensure the network’s security is to perform thorough network testing. This not only helps protect users’ assets and data ,but can also help the blockchain ecosystem thrive.
Contact our security experts at [email protected] to review cross-chain bridge source code, check for vulnerabilities, and ensure protection against malicious actors.